PrintNightmare Part III – Patching and Remediation Updates
As another week goes by, we have new updates to report regarding CVE-2021-34527 or PrintNightmare. Here’s the latest you need to know. We’ve also posted some PowerShell scripts to help apply the registry keys available over on our GitHub.
Patch Availability
Microsoft has released an out-of-band patch for PrintNightmare. You can find the appropriate KB number for your system by visiting the MSRC page on the vulnerability – CVE-2021-34527.
How Do We Further Mitigate Risk?
In addition to the patch, you still have to change three registry keys in order to secure the service, else, the system will remain vulnerable in some form or another, related to the Point and Print functionality. There’s also an alteration to one value if you’ve already set them.
The three keys you need to set are located here: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint. Chances are you will need to create the Printers key and the PointAndPrint key if you haven’t already.
The values you have to create and set in addition to installing the patch are:
- NoWarningNoElevationOnInstall = 0
This tells the OS to show a UAC prompt to confirm, provided UAC enabled - UpdatePromptSettings = 0
This tells the OS to show a UAC prompt to confirm, provided UAC enabled - RestrictDriverInstallationToAdministrators = 1
This disables delegation and non-users from installing unsigned printer drivers
Note: Earlier guidance mentioned a value of NoWarningNoElevationOnUpdate. This is actually UpdatePromptSettings. This was confusion from earlier guidance provided by Microsoft.
If you need to deploy this among multiple systems, please check out our GitHub for some PowerShell scripts to help you deploy the registry changes across systems.
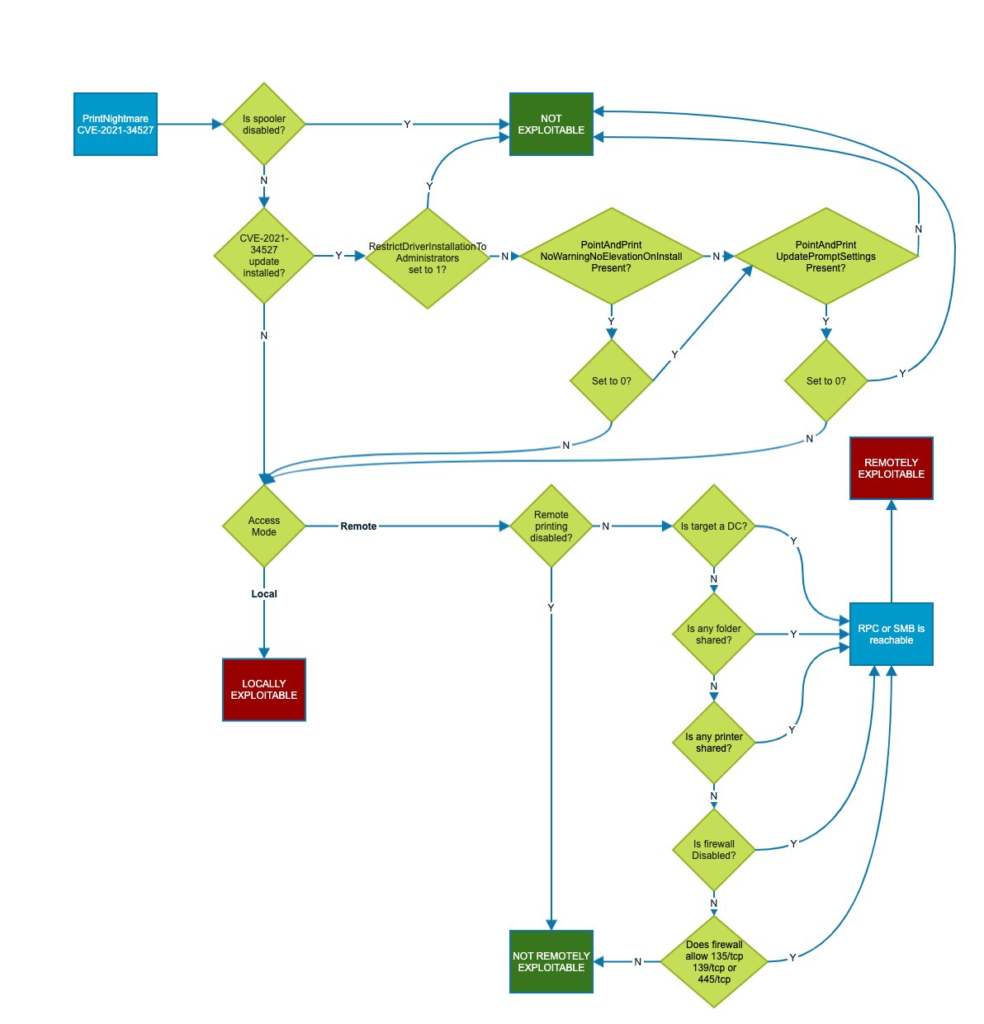
Beyond these changes, a good resource for determining if a system is vulnerable post patching is shown in this great flowchart shared below by CERT. Click the image to view it in full size.
Anything Else?
If you can’t deploy the patch yet, please still follow the mitigations based on your setup outlined in the Part II blog posted last week. We’ll be posting broad hardening options in the coming weeks to help fellow sysadmins to better secure and control the Print Spooler service. Security researchers have also mentioned that additional vulnerabilities may soon be disclosed and I’ll do my best to do a write-up on them as I can.