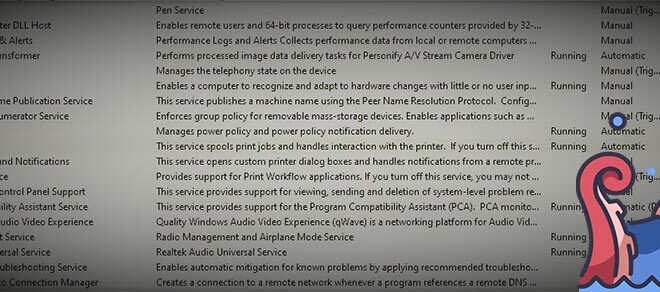
Disable Print Spooler on Domain Controllers (If You Can)
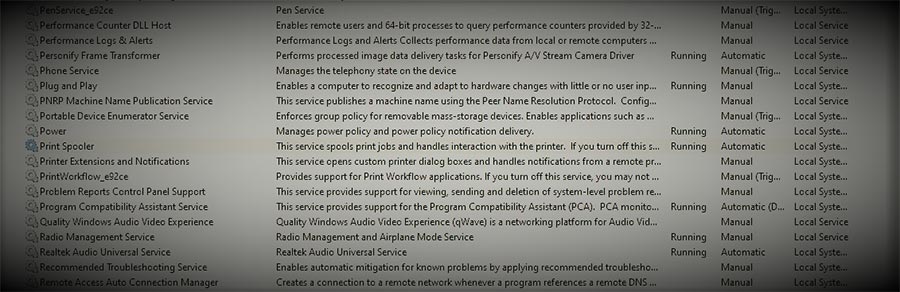
While it’s always generally best to leave domain controllers to carry their primary job of being a domain controller, some administrators end up having to tack on additional applications or services that can increase the attack surface of the system. One such service is the print spooler. The print spooler is much like print drivers and printers, spawned from the depths of hell to haunt us for eternity, or until someone makes better printers, print services, and non-proprietary ink cartridges. Basically, it’s got a lot of legacy code around it and is ripe for being used as a way to go from user to system-level privileges.
So, unless you have to host print services on one of your DC’s, it’s time to disable the service.
Editors Note: Since this original posting, we have posted a Part II that outlines how it affects all versions of Microsoft Windows and how to mitigate or detect the use of the vulnerability, and a Part III that addresses the patch and things you need to do in order to ensure it protects your systems. Keep reading below to understand the basics of the vulnerability.
What’s Actually Going On?
CVE-2021-1675, or also dubbed PrintNightmare, is a vulnerability in the Windows Print Spooler service, that was originally considered a privilege escalation vulnerability. However, a Proof-of-Concept recently demonstrated that it also doubles as a remote code execution vulnerability, and even worse, Domain Controllers are still exploitable despite this month’s updates that intended to address this vulnerability.
The first example of the positive exploitation we were able to witness came yesterday from @gentilkiwi on Twitter. You can see a video sample of one of the three working PoC’s here.
How Do I Protect Myself?
Unless you need print services on your Domain Controller, disable the service by running the following commands in PowerShell:
Stop-Service -Name Spooler -Force
Set-Service -Name Spooler -StartupType Disabled
If you have to keep print services on because let’s say you are using your domain controller as a print server, then read on.
I Have to Keep Print Services Going. How Can I Monitor For Exploitation?
If you are unable to disable print services, you can enable PrintService-Operational event logging, which is not enabled by default. To do this, run the following commands in PowerShell on the target systems.
$logDeets = Get-LogProperties ‘Microsoft-Windows-PrintService/Operational’
$logDeets.Enabled = $true
Set-LogProperties -LogDetails $logDeets
Get-LogProperties ‘Microsoft-Windows-PrintService/Operational’
You can check the status of the log at any time by using the following command in PowerShell:
Get-LogProperties ‘Microsoft-Windows-PrintService/Operational’
You can then review this log and look for Event ID 316 which will notate additions or updates to printer drivers, which includes any malicious loads based on testing.
You can also use Process Monitor to view running processes and check the path and names of EXE’s and DLL’s loaded up.
Thanks to @MalwareJake for posting this useful detail!
For even more technical detail on this, Azure Sentinel and Defender queries and more, check out Kevin Beaumont’s blog on it! Zero day for every supported Windows OS version in the wild